News

Oyster IMS and EncompaaS partner to provide information management solutions for successful AI implementations
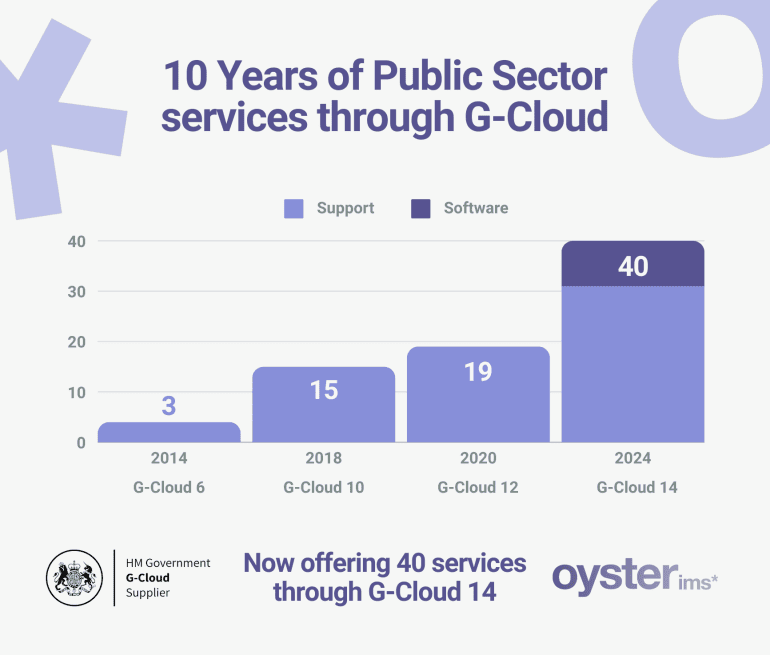
Now offering 40 services through G-Cloud 14

GDPR Compliant? Prove it!
InfoSec Spotlight feature:IoT Risk Rising
Oyster IMS extends Cybersecurity awareness training to Ireland

Welcoming new team members: Jess and Louis

First law firm obtains specialist legal services ICO certification LOCS:23

The Importance of Data Preparation in the AI Era – Webinar
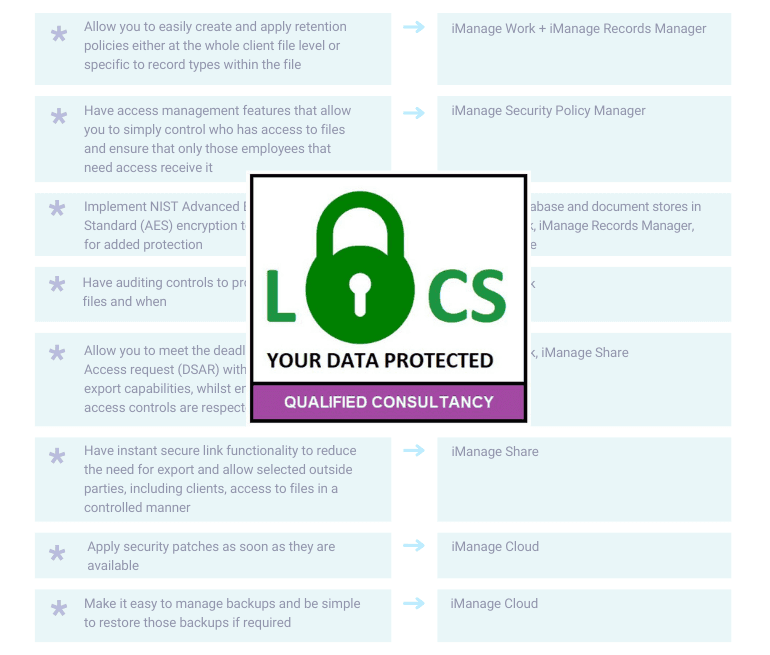
Using your legal document management system to become UK GDPR certified

